In the current digital era, where cyber threats are common for both small and large businesses, companies must make security a priority. Small and mid-sized businesses must ensure that sensitive information is secure. But how can they confirm that? Here comes the ISO 27001 certification.
Implementing tough cyber security measures is vital for protecting those from possible threats that may arise. Thus, ISO 27001- which is the basics of management system control, ensures the process of setting up, running without fail, and enhancing information security programs.
Knowing the importance and benefits of ISO 27001, we will discuss in detail how you can implement ISO 27001 along with ISMS in your small business.
Let’s get started by addressing the common cybersecurity cases!
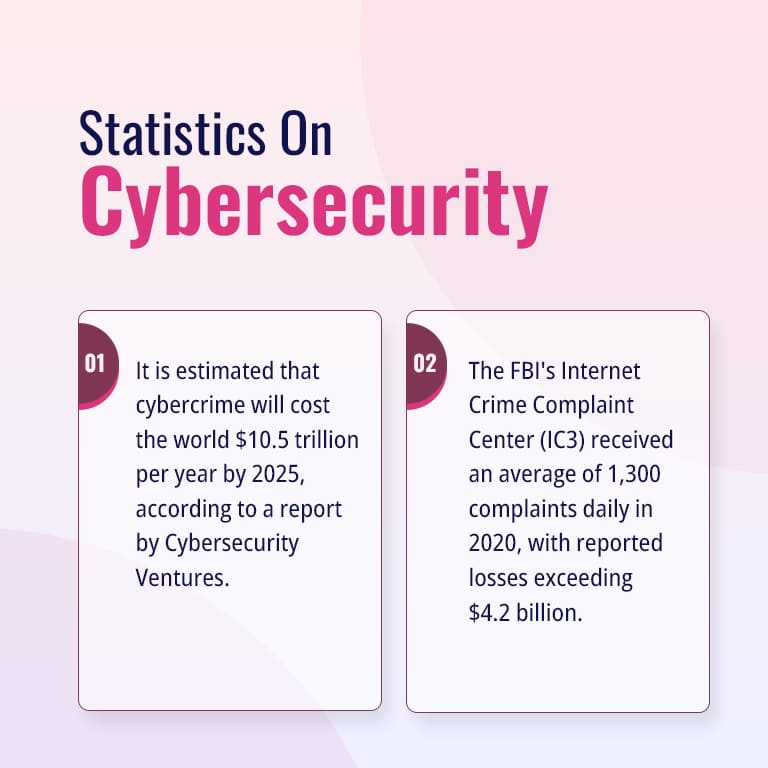
Protect your business from this malware, data breaches, and common threats today! Secure your business and get the chance to secure global growth with Socurely ISO 27001 Compliance Certification!
Understanding the ISO 27001 Checklist
ISO 27001 is the internationally recognized framework for information security management systems (ISMS). This powerful framework equips organizations with the tools and strategies to strengthen digital data, safeguarding their most precious assets from ever-evolving cyber threats and ensuring advanced security.
ISO 27001 boosts the global standard of any business. It also provides a systematic approach to managing sensitive company information, ensuring it remains secure.
The ISO 27001 compliance checklist includes key elements such as:
- Information Security Policies: Establishing a set of guidelines and rules.
- Risk Assessment and Treatment: Identifying and managing risks.
- ISMS Implementation: Setting up an Information Security Management System.
- Employee Training: Making employees aware of security protocols through training and awareness.
- Continuous Improvement: Regularly updating and improving security measures.
Why ISO 27001 Compliance Is on Demand

Currently, the ISO 27001 Certification is highly demanded as it-
- Enhances credibility and trust with clients and stakeholders.
- Assists in reducing the risk of data breaches and cyberattacks.
- Ensures compliance with legal and regulatory requirements.
- Provides a competitive advantage by demonstrating a commitment to security.
12 Steps Involved with ISO 27001 Compliance Implementation
1. Get an ISO 27001 Internal Team
- An internal team dedicated to ISO 27001 implementation ensures accountability and effective coordination throughout the process.
- They will act as the task force. In addition to working with all other stakeholders to see the compliance endeavor through completion, they will take ownership of it and lead it.
- Verify that each team member possesses the appropriate level of insight to fulfill the ISO 27001 checklist requirements.
2. Build Your ISMS
- Developing an Information Security Management System involves identifying information assets, assessing risks, defining security objectives, and expanding scope.
- The scope needs to cover the things that need to be safeguarded within your company, such as its systems, procedures, physical sites, services, and goods.
- Also before developing an ISMS, you must ascertain what kind of data you need to secure.
Some key steps of building ISMS-
- Access Expert Policies
Utilize a comprehensive library of policies developed by security experts. These policies should cover various aspects of information security, including access control, data encryption, incident response, and more. Customizing these policies to fit your organization’s context ensures relevance and effectiveness.
- Employee Engagement
Engaging your employees is crucial for the successful implementation of your ISMS. Ensure all staff are aware of the policies and understand their roles in maintaining information security. Regular training sessions and awareness programs can help reinforce this understanding and commitment.
3. Publish ISMS Policies, Procedures & Documentation
- To regulate and minimize security threats to its ISMS, the business must establish policies and processes by the extensive documentation required by the ISO 27001 implementation checklist.
You must implement the following policies:
Policy for Information Security
Policy for Mobile Devices
Policy for Teleworking and Remote Access; Access Control
Policy for Clear Desk and Screen
Appropriate Use of Data Assets Policy Secure Development Policy or Plan Supplier Management Security Policy) Policy Communications (Information Transfer) Policy
4. Perform Initial Certification
Stage 1: Design and Documentation Evaluation
The first stage of the initial certification process focuses on evaluating the design of your information security management system (ISMS). This includes:
- Assessing Documentation and Controls: Ensuring you have the necessary policies, procedures, and controls in place.
- Evaluating Process Design: Verifying that your ISMS is designed to meet ISO 27001 requirements and is ready to progress to the next stage.
Stage 2: Evidence Evaluation and Certification
In this stage, the effectiveness of your ISMS is thoroughly evaluated. This includes:
- Reviewing Evidence: Provide proof that your ISMS and controls are operational and meet ISO 27001 standards.
- Certification: Successfully passing Stage 2 results in obtaining the ISO 27001 certification, which is valid for three years from the date of initial certification.
5. Perform Surveillance Audits
To maintain your ISO 27001 certification, your business will undergo two surveillance audits over the certification period:
- Surveillance Audit 1: Conducted one year after initial certification, this audit evaluates a sample of your controls and ISMS to ensure they are functioning as intended.
- Surveillance Audit 2: Conducted two years after initial certification, this audit further ensures the ongoing effectiveness and compliance of your ISMS.
6. Going Through Recertification Audit
As the expiration of your ISO 27001 certification approaches, a recertification audit is conducted:
- Evidence Evaluation: Similar to Stage 2 of the initial certification, this audit reviews the evidence to ensure your ISMS and controls remain effective and compliant with ISO 27001 requirements.
- Renewal: Successfully passing the recertification audit extends your ISO 27001 certification for another three years, ensuring continued adherence to information security best practices.
7. Create The Statement Of Applicability (SOA)
- The SOA outlines the controls that are applicable and justifiable based on the results of risk assessment.
- All of the controls from Annex A that are relevant to your company are listed in the SOA for ISO 27001.
- Which controls the organization has selected to lessen the risks indicated should be disclosed in the SOA.
- Justifications for the addition and deletion of controls should also be included. It ought to direct users to the pertinent documentation regarding each control’s implementation.
- There are 114 security controls divided into 14 parts and 11 obligatory ISO 27001 standards (Annex A).
8. Implement ISMS Policy and Controls
- The most important task on your ISO 27001 checklist is putting the ISMS rules and procedures into practice. One popular cycle for implementation is the Plan Do Check Act (PCDA). Among its components are:
Plan: Recognize the obstacles and dangers, and record the needs and control goals.
Do: Put solutions, procedures, and technologies into practice and test them to reduce risk and operational failure.
Check: Keep track of and evaluate the ISMS. \Act performance: Adapt and enhance your ISMS in light of any outputs or shortcomings.
9. Monitor ISMS, Conduct Gap Analysis and Remediate
- Continuous monitoring, gap analysis, and remedial actions are essential for maintaining the effectiveness of the ISMS.
- Recall that continuous improvement is essential.
- After the ISMS has been remedied, compile proof that it satisfies the standard’s requirements using your ISO 27001 checklist.
10. Get Your Cloud Infrastructure Security
Securing your cloud infrastructure is a critical aspect of ISO 27001 compliance. Implement tools that can automatically monitor and configure your cloud services to ensure they adhere to security standards. Regular vulnerability assessments can identify potential risks and allow you to address them promptly.
11. Conduct Vendor Risk Management
Managing vendor risk is an essential part of maintaining a secure supply chain. Conduct thorough risk assessments for all vendors and regularly review their security practices. Storing and managing vendor security certifications and reports, such as SOC 2, ISO 27001, PCI DSS, CCPA, and GDPR, helps ensure compliance and mitigate risks.
12. Continuous Monitoring and Evidence Collection
Maintaining ISO 27001 compliance requires continuous monitoring of your information security environment. Automated tools can help by collecting evidence of compliance and alerting you to any nonconformities in real time. This proactive approach allows you to address issues quickly and maintain a high level of security.
Tips For ISO 27001 Checklist Verification
- Build Vast Understanding
Readers are encouraged to gain a comprehensive understanding of ISO 27001 to effectively implement its principles and requirements.
- Pinpoint The Scope
It is essential for businesses to clearly define the scope of their ISO 27001 implementation to ensure that all relevant areas are encompassed.
- Get Expert Help For Insights
Seeking expert assistance like Socurely can provide valuable insights and guidance throughout the ISO 27001 implementation process.
- Test The Checklist
Testing the ISO 27001 checklist ensures its efficacy and helps in identifying and addressing any potential gaps.
- Review Procedure and Policies
Regularly reviewing and updating procedures and policies is crucial to maintaining ISO 27001 compliance in the long run.
Conclusion
Achieving ISO 27001 certification is a significant step towards fortifying information security and demonstrating a commitment to safeguarding sensitive data. By understanding the implementation roadmap and diligently following the ISO 27001 checklist, small businesses can establish a resilient Information Security Management System that aligns with international standards, ensuring the protection of critical information assets.
Socurely offers comprehensive guidance and support for businesses seeking ISO 27001 certification. Their expert team assists in navigating the certification process seamlessly.







